Cerber Ransomware
Another variant of the Cerber ransomware family has received new strategies to make itself harder to distinguish by endpoint security software that utilizations machine learning for discovery.It is presently utilizing another loader intended to dig out a typical procedure where the code of Cerber keeps running.
Cybercriminals are utilizing a subtle strategy to guarantee
that Cerber ransomware makes it past hostile to infection scanners and infects
casualties' computers.
Stop Cerber Ransomware Using Free Malware Removal Tool
Utilizing a procedure known as double cushioning alongside
the Magnitude Exploit Kit—which is notable in cybercriminal circles—ransomware
wholesalers are falsely swelling the extent of Cerber records before they are
executed.
The payload's increased size permits the ransomware to skirt its way around security software that can't check more significant documents for advanced dangers, as indicated by analysts at security software firm Malwarebytes.
The payload's increased size permits the ransomware to skirt its way around security software that can't check more significant documents for advanced dangers, as indicated by analysts at security software firm Malwarebytes.
Associations can prepare for abuse units like Magnitude by
trying to introduce the most recent security fixes and updates to working
frameworks and applications.
Cerber raised its revolting head March a year ago and had
quickly snatched market share by angrily advancing and utilizing distinctive
assault vectors and dispersions channels. It spreads through phishing messages,
yet also uses misuse units.
Related: What is junk cleaner and how to use a junk remover in PC
In August 2016, Invincea analysts found that Cerber was
being appropriated by Betabot, which was outlined as a saving money data taking
Trojan yet reused for ransomware.
As of late, Cyren specialists detailed that Cerber is being dropped by Kovter, a tick extortion Trojan which was falling Locky a while prior.
As of late, Cyren specialists detailed that Cerber is being dropped by Kovter, a tick extortion Trojan which was falling Locky a while prior.
Pattern Micro reports that the new loader was essential
since machine learning security code identify malicious records given
highlights rather than marks.
The new bundling and stacking instrument utilized by Cerber can cause issues for static machine learning approaches– i.e., techniques that break down a record with no execution or copying.
As it were, the way Cerber is bundled could be said to be intended to sidestep machine learning document recognition.
For each new malware discovery procedure, a comparable avoidance method is made out of need.
The new bundling and stacking instrument utilized by Cerber can cause issues for static machine learning approaches– i.e., techniques that break down a record with no execution or copying.
As it were, the way Cerber is bundled could be said to be intended to sidestep machine learning document recognition.
For each new malware discovery procedure, a comparable avoidance method is made out of need.
The uplifting news, the specialists say, is this new
avoidance method can be vanquished by security approaches that utilize numerous
layers of assurance, because the assault has various shortcomings, for example,
the utilization of an unloaded.DLL document.
Arrangements that don't excessively depend on machine learning can even now demonstrate dominant against this danger.
Arrangements that don't excessively depend on machine learning can even now demonstrate dominant against this danger.
What's more, obviously you need to step all your end-clients
through new-school security mindfulness preparing, with the goal that they
detect the phishing messages when they endure every one of the channels.
We're eager to report another asset to you, our new Ransomware Simulator.
How weak is your system against ransomware? Awful folks are
continually turning out with new forms of ransomware strains to dodge
discovery.
Related: Trovi.com Browser Redirect Virus Removal Tool
Is your system successful in blocking ransomware when workers succumb to social designing assaults KnowBe4's Ransomware Simulator "RanSim" gives you a speedy take a gander at the viability of your current system assurance?
Rankin will reproduce ten ransomware infection situations and show you if a workstation is helpless against infection.
Related: Trovi.com Browser Redirect Virus Removal Tool
Is your system successful in blocking ransomware when workers succumb to social designing assaults KnowBe4's Ransomware Simulator "RanSim" gives you a speedy take a gander at the viability of your current system assurance?
Rankin will reproduce ten ransomware infection situations and show you if a workstation is helpless against infection.
How it functions
The most current Cerber appropriation crusade starts with
Magnitude EK, an infamous endeavor pack which mishandles known software defects
keeping in mind the end goal to download malware onto powerless machines.
Size EK has a notoriety for misusing Microsoft Internet Explorer vulnerabilities, however at times gets to frameworks through Adobe Flash Player shortcomings.
Size EK has a notoriety for misusing Microsoft Internet Explorer vulnerabilities, however at times gets to frameworks through Adobe Flash Player shortcomings.
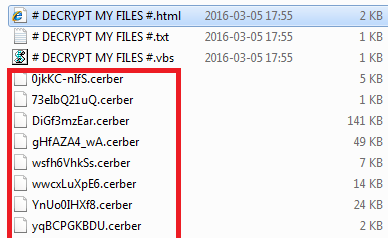
Found in mid-2016, Cerber is a document scrambling software
that exploits infection by checking the nation code of a machine.
Related: EasyPDFCombine Browser Virus Removal Tool and Guide
If the casualty's computer isn't situated in Russia, Central Asia, or Eastern Europe, Cerber spares a duplicate of itself under a haphazardly produced executable name.
It at that point heightens its benefits previously scrambling the machine's records and spreading itself crosswise over systems.
Related: EasyPDFCombine Browser Virus Removal Tool and Guide
If the casualty's computer isn't situated in Russia, Central Asia, or Eastern Europe, Cerber spares a duplicate of itself under a haphazardly produced executable name.
It at that point heightens its benefits previously scrambling the machine's records and spreading itself crosswise over systems.
Cerber has been broadly accessible through
ransomware-as-a-benefit (RaaS). That implies pretty much anybody—even
cybercriminals who aren't, in fact, keen—can dispatch an assault for an
expense. This availability no uncertainty helped Cerber outperform Locky as
most broadly utilized ransomware conveyance in 2016.
Shield yourself from advancing ransomware dangers
Malwarebytes scientist Jerome Segura says organizations
should be worried about adventure packs like Magnitude.
"While Magnitude EK has an extremely limit circulation
channel, it remains an intriguing endeavor unit because does it have its
entryway, as well as keeps on advancing with different traps," Segura
clarifies in a blog entry.
"The double cushioning method demonstrates a push to
sidestep certain security scanners that will disregard documents over a
specific size.
In any case, this does not keep the malicious paired (regardless of how enormous) to run its course and completely infect a machine."
In any case, this does not keep the malicious paired (regardless of how enormous) to run its course and completely infect a machine."
Related: Wallet Ransomware decryptor & .wallet File Extension Guide
Organizations might have the capacity to keep a Magnitude
assault by actualizing a complete fix administration technique and by directing
eternal security mindfulness preparing with representatives.
But at the same time, it's imperative to move down all information and store it in a safe area on the off chance that the ransomware assault is effective.
But at the same time, it's imperative to move down all information and store it in a safe area on the off chance that the ransomware assault is effective.
Cerber Ransomware develops
The most recent variant of Cerber likewise varies from its
prior emphasis in a way that in spite of the fact that the method of assault is
same, i.e., conveyed through the malicious phishing email; the messages contain
a connection to Dropbox that downloads and self-extricates the malware payload
itself.
The accompanying stream graph can enable you to comprehend the idea better.
Once introduced, the malware form runs a personality check
to confirm if it is running on a virtual machine or sandbox.
If anybody of it is recognized, the malware promptly quits hurrying to keep away from the Cerber code being identified and dissected.
It has been discovered that digital security specialists regularly take after this usual way of doing things to examine malware and prevent it from spreading all through the system.
Related: Yet Another Cleaner (YAC) Virus Removal Guide
If anybody of it is recognized, the malware promptly quits hurrying to keep away from the Cerber code being identified and dissected.
It has been discovered that digital security specialists regularly take after this usual way of doing things to examine malware and prevent it from spreading all through the system.
Related: Yet Another Cleaner (YAC) Virus Removal Guide
Pattern Micro Inc recognizes, new and developing dangers
will dependably endeavor to get around the most recent arrangements.
Like this, clients ought to abstain from depending on any single way to deal with security. A proactive, multilayered way to deal with security can end up being more powerful.
Savvy Protection suites and other security apparatuses can shield clients and organizations from these dangers by distinguishing malicious documents, and spammed messages and additionally obstructing all related malicious URLs.
Like this, clients ought to abstain from depending on any single way to deal with security. A proactive, multilayered way to deal with security can end up being more powerful.
Savvy Protection suites and other security apparatuses can shield clients and organizations from these dangers by distinguishing malicious documents, and spammed messages and additionally obstructing all related malicious URLs.
Cerber Ransomware Enhanced
Cerber, one of, if not the most common and harming types of
ransomware to date, has as of late been upgraded.
The new form incorporates two extra avoidance strategies. The principal abstains from being identified by the kind of machine learning apparatuses that depend entirely on static examination.
These devices inspect a protest without executing it—searching for known malicious structures and substance inside the record.
The new form incorporates two extra avoidance strategies. The principal abstains from being identified by the kind of machine learning apparatuses that depend entirely on static examination.
These devices inspect a protest without executing it—searching for known malicious structures and substance inside the record.
Avoidance Tactics
The new Cerber ransomware variation makes this troublesome
because it utilizes self-separating documents, which for this situation, don't
have any noticeable malicious structures or substance.
The malicious payload is covered up inside a parallel record that resembles a customary setup document.
Related: What is Tuvaro Toolbar? How To Remove Tuvaro Search Engine
Malware identification items that don't execute Cerber won't identify the malicious code that is covered up in the indicated arrangement record.
Since they perform just a static investigation of Cerber, they won't see anything malicious.
The malicious payload is covered up inside a parallel record that resembles a customary setup document.
Related: What is Tuvaro Toolbar? How To Remove Tuvaro Search Engine
Malware identification items that don't execute Cerber won't identify the malicious code that is covered up in the indicated arrangement record.
Since they perform just a static investigation of Cerber, they won't see anything malicious.
The second avoidance strategy searches for the nearness of a
sandbox or virtual machine. On the off chance that either is discovered, Cerber
won't execute.
Since various malware discovery items exist inside a sandbox or virtual machine, the new Cerber variation will identify their essence and avoid running anything malicious.
Since these discovery apparatuses can't watch anything that seems dangerous, they discharge the record consequently permitting the malware to enter the system where it in this way executes and introduces the ransomware.
Since various malware discovery items exist inside a sandbox or virtual machine, the new Cerber variation will identify their essence and avoid running anything malicious.
Since these discovery apparatuses can't watch anything that seems dangerous, they discharge the record consequently permitting the malware to enter the system where it in this way executes and introduces the ransomware.
Profound Content Inspection
Since Lastline doesn't resemble a sandbox or contain any
virtual machine ancient rarities, Cerber can't recognize its quality.
Furthermore, because Lastline's Deep Content Inspection™ utilizes machine learning innovation that performs both static and dynamic investigation, the malware is ultimately executed.
Lastline inspects each guideline implemented inside the CPU, including code executed by the malware, working framework, portion, or different programs.
Related: Onclickads – Virus removal Tool and Protection Guide
Lastline has finish permeability and can to see the more significant part of the malicious capacities and harming practices of Cerber ransomware, and along these lines will obstruct the record and keep the malware from being executed.
Furthermore, because Lastline's Deep Content Inspection™ utilizes machine learning innovation that performs both static and dynamic investigation, the malware is ultimately executed.
Lastline inspects each guideline implemented inside the CPU, including code executed by the malware, working framework, portion, or different programs.
Related: Onclickads – Virus removal Tool and Protection Guide
Lastline has finish permeability and can to see the more significant part of the malicious capacities and harming practices of Cerber ransomware, and along these lines will obstruct the record and keep the malware from being executed.
This ransomware variation does not overcome machine learning
as a rule, but instead, it will ruin malware discovery devices that have a
feeble machine learning execution.
Cerber Ransomware interruption technique
Cerber Ransomware duplicates its file(s) to your hard
circle. Its run of the mill document name is (random name).exe.
At that point, it makes new startup key with name Cerber Ransomware and esteem (random name).exe.
You can likewise discover it in your procedures list with name (random name).exe or Cerber Ransomware. Also, it can make the envelope with name Cerber Ransomware under C:\Program Files\ or C:\ProgramData.
At that point, it makes new startup key with name Cerber Ransomware and esteem (random name).exe.
You can likewise discover it in your procedures list with name (random name).exe or Cerber Ransomware. Also, it can make the envelope with name Cerber Ransomware under C:\Program Files\ or C:\ProgramData.





I like the way you explain an effortless Cerber ransomware removal tool. It is a useful piece of information. I am eager to know about French101 ransomware.
ReplyDeleteDownload Malwarebytes latest Premium version 👇
ReplyDeleteDownload Malwarebytes Premium version for pc,tablet and laptop
Follow my social networks for funny memes and odd news
Facebook page 👇
follow Facebook page
Twitter👇
Join Twitter
Telegram👇
Join Telegram
I value the useful information you have offered. You must read this article Farnsworth Lantern Test for Color Blindness. In place of the Ishihara color vision test, it is an alternative.
ReplyDelete